There are several ways to deploy videoconferencing within an organization. Whether it’s in the public cloud, private cloud, or an on-premise solution, each deployment meets a specific need and has its own advantages. Definition of Cloud-Based Videoconferencing...
What is an on-premise video conferencing software?
An on-premise video conferencing software enhances communication security and data control. Definition of an on-premise video conferencing An on-premise video conferencing software refers to an audio and video communication solution deployed and hosted on an...
What is an out-of-band communication?
Used in critical contexts, out-of-band communications contribute to protecting exchanges and ensuring the continuity of business activities for organisations in crisis situations. Definition An out-of-band communication refers to communications made outside of the...
Secure video conferencing for lawyers: criteria and privacy issues
Lawyers utilise secure video conferencing for exchanges with their clients or peers. But what are the criteria to ensure the security of communications and the data of the individuals involved in legal proceedings? Confidentiality of video conferencing for lawyers The...
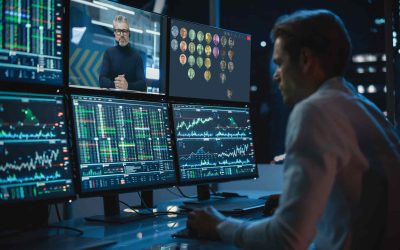
Finance: why is secure video conferencing your crisis management ally?
As prime targets for cyberattacks, companies in the finance, banking, and insurance sectors must be prepared to manage major crises. It is by reacting quickly and in a coordinated manner that they will ensure their business continuity. A dramatic increase in cyber...
How to avoid “zoombombing” during an online meeting?
"Zoombombing" in video conferencing is still going strong. It disrupts increasingly strategic online meetings, often with malicious intent. To avoid this, video conferencing security must be maximised at all levels. What is "zoombombing" in online meeting?...