Cyberwarfare, also known as hybrid warfare, is redefining the rules and dimensions of international conflicts. Its actors and consequences are numerous. What are the impacts on the security of states and organizations?
Définition
Cyberwarfare commonly refers to a set of offensive and defensive operations that take place in cyberspace, exploiting the interconnectedness and vulnerability of digital infrastructures.
These global-scale operations now take many forms and target various goals (computer sabotage, subversion, cyber espionage…), sometimes even mobilizing dedicated military resources.
The uniqueness of cyberwarfare lies both in the difficulty of attributing attacks and in the rapid evolution of the methods used.
The Strategic Dimension of Cyberwarfare
Conducting operations in cyberspace also represents a strong strategic dimension for state power. Indeed, nations can exert their influence and act without resorting to conventional military force.
Moreover, one of the criteria for evaluating a nation’s cyber power is its ability to use digital technologies to achieve its national and international objectives, particularly in defense and offense.
Example: The Russia-Ukraine Cyberwar
Since Russia’s invasion of Ukraine in February 2022, the war between the two countries has intensified in cyberspace. Recently, Ukraine’s Economic Security Council published a study titled “Cyber, Artillery, and Propaganda,” which analyzes Russian operational methods.
The conclusion is clear: the Russia-Ukraine conflict is the world’s first large-scale cyberwar. It directly impacts Ukraine, with systematic Russian cyberattacks on state offices, critical infrastructure, and even media outlets.
However, the “cyberwar” also affects Ukraine’s allied nations. In Europe, numerous espionage and disinformation attacks, originating from Russia, have been identified in recent months.
The Various Methods Used
Cyber Espionage
Cyber espionage is one of the primary impacts of geopolitical upheavals and cyberwarfare. It involves stealing confidential and strategic data, sometimes classified, from a nation or organizations.
Cybercriminals can intercept information communicated via video conferencing or messaging, for example, during an election or conflict, to obtain sensitive information.
Espionage can also aim to undermine a company’s competitive advantage by intercepting documents or data shared online. Their compromise affects not only a company’s intellectual property but also the scientific and technical potential of the nation.
Read the article: What Are the Targeted Information in Industrial Espionage?
Sabotage
Another method used in full-scale cyberwarfare is computer sabotage. This type of attack generally targets critical infrastructures or installations. Their computer and communication systems, networks, or even databases are targeted to compromise their functioning. The objectives may be to harm a nation’s security and economy.
Computer sabotage takes many forms:
• Distributed denial-of-service (DDoS) attacks to overwhelm servers,
• Malware to infect and damage a system or network,
• Or phishing to trick a user into taking actions that compromise security.
The supply chain (subcontractors, partners, suppliers…) of large companies is also a prime target for computer sabotage. Cyber attackers tend to indirectly disrupt critical organizations by affecting their ecosystem.
Disinformation
Particularly used during election periods, subversion operations aim to influence public opinion about a personality, political party, or institution. Disinformation campaigns, especially on social networks or via the media, are the most visible part. At a national level, disinformation leads to political instability. In companies, it can disrupt governance.
In 2024, a year particularly busy politically, the risks of disinformation are high. According to the “Global Risks 2024” report published by the World Economic Forum, misinformation and disinformation are the two main short-term risks.
Par ailleurs, une enquête de la société de conseil néerlandaise Trollrensics, commandée par la délégation néerlandaise du groupe Socialistes et Démocrates au Parlement européen, a récemment démontré « qu’un vaste réseau coordonné de comptes influençait le discours public sur les réseaux sociaux en Allemagne et en France à l’approche des élections européennes [de juin 2024].» en diffusant des propos anti-vax, anti-LGBT et pro-russes. Selon le rapport, certains de ces comptes ont été créés suite à l’invasion de l’Ukraine par la Russie, voire même avant, indiquant une activité plus large et ancienne.
Furthermore, a study by the Dutch consulting firm Trollrensics, commissioned by the Dutch delegation of the Socialists and Democrats group in the European Parliament, recently revealed that “a vast coordinated network of accounts influenced public discourse on social networks in Germany and France ahead of the European elections [in June 2024].” by spreading anti-vax, anti-LGBT, and pro-Russian rhetoric. According to the report, some of these accounts were created following Russia’s invasion of Ukraine, or even before, indicating broader and older activity.
The Means Employed in Cyberwarfare
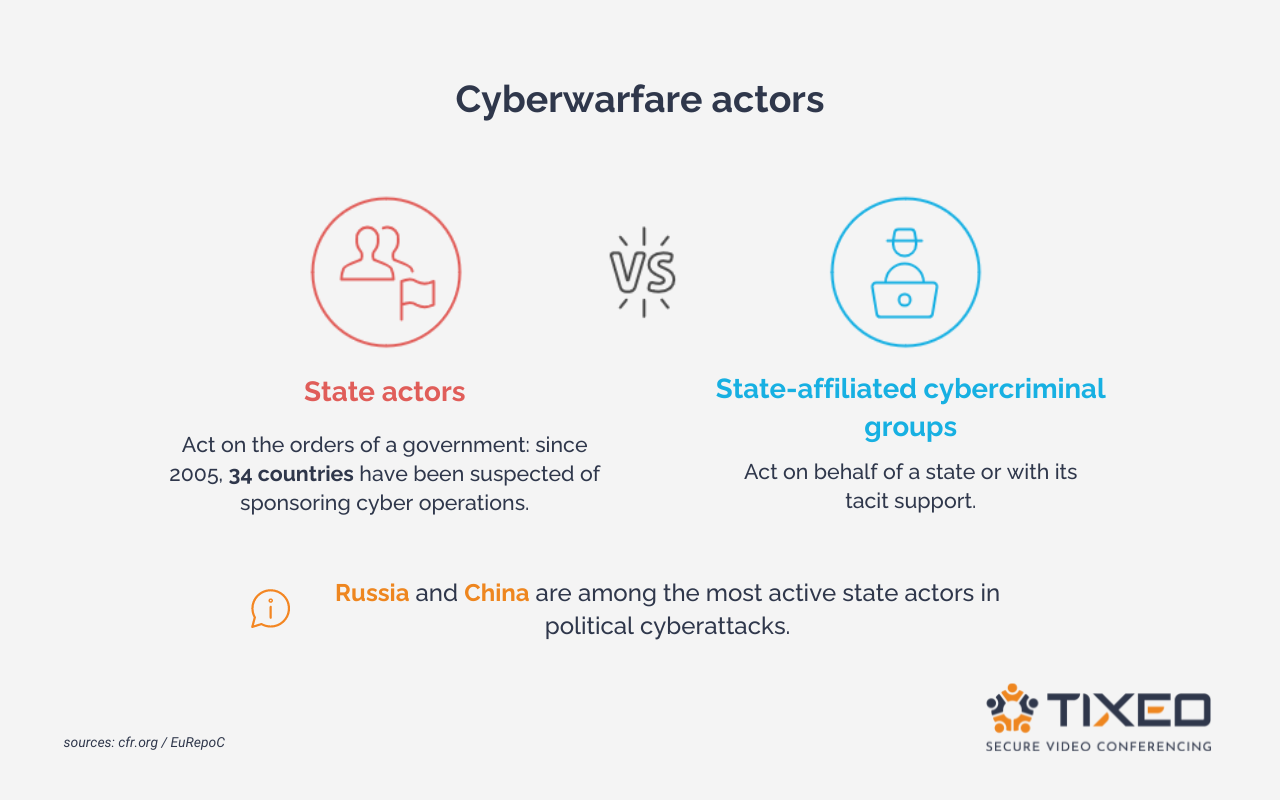
State Actors
Some groups of cybercriminals operate directly under the authority of a government.
According to cfr.org: “since 2005, 34 countries have been suspected of sponsoring cyber operations. China, Russia, Iran, and North Korea are believed to be responsible for 77% of all suspected operations.” In full-scale cyberwarfare, the number of states involved in cyber threats is increasing, with known state actors like APT33 in Iran, APT10 in China, Lazarus Group in North Korea, or Sandworm in Russia.
These last two nations are particularly active in the field. The European Repository of Cyber Incidents (EuRepoC) database indicates that since the beginning of the century, a quarter of the detected political cyberattacks have been deployed from China (11.9%) and Russia (11.6%).
In an information sheet (published on the Internet Crime Complain Center website), CISA, the National Security Agency (NSA), and the FBI warn critical organizations about “the urgent risk posed by cyber actors sponsored by the People’s Republic of China (PRC).” These actors, under the name “Volt Typhoon,” work to disrupt essential services in response to geopolitical tensions. These actions can also impact NATO member countries. As the organization warns on its website, “China’s hybrid or cyber-malicious operations threaten NATO’s security.”
Para-State Cybercriminal Groups
Para-state cybercriminal groups do not operate directly under the orders of a state but usually act on their behalf or with their support.
This is the case of the UNC1151 group, linked to the Belarusian government, which has been conducting online disinformation operations for several years, particularly to discredit NATO in the Baltic countries. Since 2017, their information warfare campaign, called Ghostwriter, has been spreading content hostile to the Atlantic Alliance, notably fake news about the deployment of nuclear weapons.
Exemple aussi en Iran où, suite au conflit au Proche-Orient, des hackeurs affiliés au gouvernement iranien ont interrompu plusieurs chaînes de télévision européennes, diffusées aux Emirats arabes unis, pour diffuser un faux journal télévisé généré par IA.
An example in Iran is where, following the conflict in the Middle East, hackers affiliated with the Iranian government disrupted several European television channels broadcast in the United Arab Emirates to air a fake AI-generated news report.
Russian Hackers: Major Players
Russia and its cybercrime actors are major players in cyberwarfare. In recent years, several Russian cyberattacks have targeted Ukraine but also NATO member or partner countries.
In 2017, a Russian sabotage operation against Ukraine paralyzed banks, Kyiv’s airport and metro, railways, media outlets, postal services, energy and gas providers, mobile phone operators, and even hospitals… Russian hackers even managed to affect the French and American economies: companies like Saint-Gobain, BNP, FedEx, or Mondelez were severely affected. The cause: the NotPetya malware, which took 7 minutes to paralyze 55,000 machines, more than 130 per second, at Maersk, a giant in maritime transport.
More recently, in December 2023, a cyberattack via malware targeted Ukraine’s leading telecom operator. 24 million citizens in the country found themselves without Internet connection.
Three Main Consequences
Social and Economic Impacts
By targeting more or less critical organizations, cyberwarfare causes direct financial losses, notably through the theft of confidential data, ransomware attacks, or acts of computer sabotage. These cyberattacks generally result in activity disruptions and can harm a company’s reputation.
In key sectors such as energy, telecommunications, or public administration, acts of cyberwarfare also have significant consequences. Power outages, internet disconnections, or inaccessibility of public services disrupt the social and economic balance of a nation.
Political Destabilization
Cyberwarfare is first and foremost political and geopolitical. Disinformation and cyber espionage operations often aim to destabilize politically. Such acts, like the subversion campaigns on social networks ahead of the last European elections, can seriously influence the course and outcome of an election and thus disrupt democratic processes.
Increase in Cybersecurity Investments
The rise in cyber threats, such as espionage and sabotage, is prompting more and more organizations to strengthen their cybersecurity. Indeed, cyberattacks are diversifying and becoming more sophisticated, making them difficult to avoid. In critical entities, as identified by the NIS 2 Directive, cyber resilience is becoming essential. This involves organizations implementing strategies to:
- map the cyber risks inherent to their sector of activity,
- anticipate crises,
- and organize business continuity.
These cyber resilience strategies must be supported by organizational measures (staff training, crisis management teams…) and technical measures (network segmentation, use of backup communication tools…).
What Are Some Famous Cyberwarfare Attacks in History?
1. Stuxnet (2010)
Stuxnet is arguably one of the most famous and sophisticated cyberattacks in history. This computer worm was designed to target the centrifuges used in Iran’s nuclear program. Stuxnet has been widely attributed to the United States and Israel, and it successfully damaged around 1,000 centrifuges, thus slowing down Iran’s nuclear progress.
Learn more: Stuxnet: A Dutch Engineer Behind the Infection
2. Cyberattaque contre l’Estonie (2007)
Estonia, one of the world’s most digitized countries, was the target of a massive cyberattack in 2007. Government websites, banks, media outlets, and other critical infrastructures were paralyzed by distributed denial-of-service (DDoS) attacks. This attack was widely attributed to Russian actors, though it was never officially proven.
Learn more: Cyberwarfare: A Look Back at the 2007 Cyberattack on Estonia
3. NotPetya (2017)
Initially launched against targets in Ukraine, the NotPetya attack quickly spiraled out of control and spread worldwide, causing billions of dollars in damage. NotPetya is a ransomware masquerade that paralyzed the computer systems of numerous international companies, including Maersk, FedEx, and Saint-Gobain. This attack has been attributed to the Russian Sandworm group.
Learn more: Reflecting on NotPetya: A Milestone in Cyberwarfare History
4. Sony Pictures Hack (2014)
In November 2014, Sony Pictures Entertainment was the target of a massive cyberattack attributed to the Lazarus Group, a North Korean hacker collective. The attackers stole sensitive data and released embarrassing information. The attack was allegedly a response to the upcoming release of “The Interview,” a satirical comedy about North Korea.
Learn more: Cultural Hacking: A Case Study of the Sony Pictures Hack
5. Opération Aurora (2009-2010)
Operation Aurora is the name given to a series of cyberattacks carried out against several major American companies, including Google, Adobe, and Dow Chemical. These attacks, attributed to Chinese actors, aimed to steal industrial secrets and sensitive information. The attack on Google led the company to threaten to withdraw from the Chinese market.
Learn more: Operation Aurora (2009): A Cyber Counter-Espionage Campaign?
Read our white paper on videoconferencing security in the midst of cyberwarfare
FAQ :
Cyberwarfare refers to a set of offensive and defensive operations conducted in cyberspace, exploiting the vulnerabilities of digital infrastructures to achieve various objectives, such as sabotage or cyber espionage.
The main actors include states (such as Russia, China, and Iran) as well as cybercriminal groups operating under the authority or with the support of these governments.
The difficulty of attributing cyberwarfare attacks lies in the anonymity of cyberspace and the use of complex methods that obscure the real perpetrators of the attacks.
Cyberwarfare can lead to economic disruptions, outages of essential services, and political destabilization through disinformation and sabotage campaigns.
Nations are increasingly investing in cybersecurity by developing cyber resilience strategies, training dedicated teams, and adopting advanced technical measures to protect their critical infrastructures.

